I’ve had a number of issues with cookies lately, which means I’ve had a number of issues with security. What else does this mean, I’m working with things that people are trying to keep quiet. If you follow this blog a little, you’ll recall the PS_TOKEN saga (which is still ongoing). At this stage we might be using the F5 to not send the token to JDE and therefore prevent the login issues. How painful is that!
We’ve had another interesting scenario, once again involving cookies in iframes. My client has a 3rd part application for AP scanning. This write’s URL’s to PO’s, so that the original PO can be viewed from JD Edwards in the media object iframe. Sure, this is nice, but it was not working with some painful “to and fro” of cookies. Once again I was using the F12 functionality in IE9 (yes – I know – old school) to work out what was going on.
I found that the iframe cookie is the “poorer cousin” of the browser, especially where ie9 is concerned. Once again, chrome just keeps trucking – loves Iframes and mauls their cookies… I like chrome more and more.
At the end of the day, I was able to see in the security. Settings -> safety -> web page privacy settings… then sites. Make sure that the sites that are in the URL in media objects are listed as safe / allow cookies (mine were blocked).
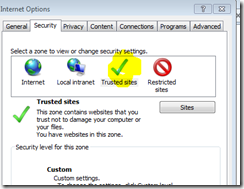
The other thing that I did was (which was easier). Was go to trusted sites and add this site https://apscanning.stuff.things to the list of trusted sites.
Now I can click on my URL type attachment and go straight into the scanning application! The browser allows the iframe to load the cookie and treats it like a peer.
Note that this was analysed by using a combination of network trace in development tools in internet explorer and a little bit of “Microsoft Network Monitor 3.4”. I must admin that for a simple and free tool, this is really good for numpties like me to analyse traffic.

No comments:
Post a Comment