There is no typo in the page title, it’s possible to support long usernames and long passwords with JD Edwards using a simple IIS application that we can provide for you. The myLUNCH (Long UserName Credential Handler) product not only has one of the best names in the industry, it also works like a treat!
MyLunch is able to authenticate users using their LDAP (Microsoft Active Directory) username and password, not matter what the length or complexity! The product can either authenticate natively (good for some users) or via LDAP on a user by user basis.
The product is a very simple IIS site that can be setup in hours, it can also do load balancing of your production web servers using it’s built in multiple destination functionality.
Instead of getting the JDEdwards login page, we direct the user to a New login page asking for LDAP credentials. If the user attempts to login, the software firstly determines if the username is an LDAP user or a JD Edwards authentication user. As soon as this is determined, the authentication method is executed against the relevant target. The user is then simply signed into JD Edwards.
This can be done via SSL or standard sockets:
Enter your domain username and password of any length
You are signed into E1.
When you sign out you are back to the customised login page. It’s that simple.
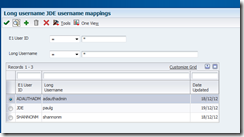
We give you the ability to map your long usernames with your JD Edwards usernames:
Any changes of mapping are written to the standard security audit tables (F9312).
This works with shortcuts too.
So, this is a simple JD Edwards solution for allowing users with long usernames and passwords to log into JD Edwards. Remember that ANY solution will have some username translation, as the DD field in e1 for USER (audit stamps, users etc) is only 10 characters long.
The software includes the ability to bulk load the JD Edwards tables with the usernames and mappings, so you can convert to AD authentication in minutes, not days.
Contact me at shannon. moir @ myriad-it . com for a demo. I plan to post a youtube video soon.


2 comments:
Looks great! Managed to obtain the same result with OAM (and WNA) but took much longer than a few hours!
How much are the licences for this product?
Thanks MM, we think that it's pretty cool too. The product is 5K AUD for the buy and then maintenance at 22%. You could add up your administrative password changes in a year and already you are saving money!
Post a Comment