Actually, what are we trying to achieve. I have a linux enterprise server and I want my users to be able to put and get interoperability files to this machine. Right, I want it to be secure too, I want to be able to control it. So I probably need samba for sharing and then some moire tricks for authentication to MAD. I need to get samba working for an OEL box. To get SAMBA working, I want to use domain credentials. Let’s be honest, doing linux properly involves using LDAP for credential handling.
setting up samba and winbind for windows credential handling in linux.
so u have a share in linux that you want to expose to windoze land, easy... kerberos, samba and winbind will help you.
First, get kerberos working... how?
vi /etc/krb5.conf
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log[libdefaults]
default_realm = MYDOMAIN.LOCAL <- you define this later
dns_lookup_realm = true
dns_lookup_kdc = true
ticket_lifetime = 24h
forwardable = yes[realms]
MYDOMAIN.LOCAL = { <-this is the one that you defined, your LDAP servers
kdc = ssydads01.MYDOMAIN.local
admin_server = ssydads01.MYDOMAIN.local
default_domain = MYDOMAIN.local
kdc = ssydads01.MYDOMAIN.local
}[domain_realm] <-set up some aliasing
.MYDOMAIN.local = MYDOMAIN.LOCAL
MYDOMAIN.local = MYDOMAIN.LOCAL[appdefaults]
pam = {
debug = false
ticket_lifetime = 36000
renew_lifetime = 36000
forwardable = true
krb4_convert = false
}
But what now, you need to ensure that you have the latest packages for winbind etc.
you'll need samba 3.6.7, well at least - I did and so did Geoff!
Geoff has kindly told me which order to install / Update packages in with the handy little addendum:
- rpm -ivh libwbclient0-3.6.7-44.el5.x86_64.rpm
- rpm -Uvh libsmbclient0-3.6.7-44.el5.x86_64.rpm
- rpm -ivh libsmbclient-devel-3.6.7-44.el5.x86_64.rpm
- rpm -ivh libwbclient-devel-3.6.7-44.el5.x86_64.rpm
- rpm –ivh –replacepkgs –replacefiles samba3-client-3.6.7-44.el5.x86_64.rpm
- rpm -ivh –replacepkgs –replacefiles samba3-winbind-3.6.7-44.el5.x86_64.rpm
- rpm -ivh –replacepkgs –replacefiles samba3-3.6.7-44.el5.x86_64.rpm
- rpm -ivh –replacepkgs –replacefiles samba3-utils-3.6.7-44.el5.x86_64.rpm
- rpm -ivh samba3-doc-3.6.7-44.el5.x86_64.rpm
- rpm -ivh samba3-debuginfo-3.6.7-44.el5.x86_64.rpm
Note that you will not need all of the –replacepkgs if you first uninstall samba
Once this has been done right, you should be able to kinit command. Note that this is your CaSe sensitive realm name from krb5.conf
kinit user@REALM
kinit shannon@MYDOMAIN.LOCAL
The system will ask you for a password - nice!
So now that you have kerberos functional, time to get winbind and samba working
service smb restart to restart all of your smb related services
using:
> net ads testjoin
you’ll probably get:
ads_connect: No logon servers
Join to domain is not valid: No logon servers
That is because you need to fill out your SMB.conf file.
vi /etc/samba/smb.conf
#Global parameters
[global]
security = ads
realm = MYDOMAIN.LOCAL
max protocol = smb2
server string = VSYDJDE04
workgroup = MYDOMAIN
netbios name = VSYDJDE04
encrypt passwords = Yes
auth methods = guest winbind:ntdomain <--help you use windoze permissions on share
# guest account = guest
max xmit = 65535
name resolve order = wins host
socket options = TCP_NODELAY SO_RCVBUF=131072 SO_SNDBUF=131072
os level = 16
preferred master = No
domain master = No
local master = No
use sendfile = No
unix charset = UTF8
winbind use default domain = yes
create mask = 0700
directory mask = 0700
aio read size = 65536
aio write size = 65536
# aio read size = 32768
# aio write size = 32768
idmap config * : range = 10000-20000
idmap config * : backend = tdb
idmap config MYDOMAIN : default = yes
idmap config MYDOMAIN : range = 100000-200000
idmap config MYDOMAIN : backend = rid
[test2]
path = /test
available = yes
browseable = yes
follow symlinks = yes
read only = no
public = yes
max connections = 0
[interop]
path = /u01/app/jdedwards/interop
available = yes
browseable = yes
follow symlinks = yes
read only = no
public = yes
max connections = 0
service smb restart
then:
> net ads join -U domainusername
and enter your password.
net ads join -U smoir
Enter smoir's password:
Using short domain name – MYDOMAIN
Joined 'VSYDJDE03' to realm 'mydomain.local'
if this has all worked, you have all of the net ads commands at your fingertips. Remember that if you are logged in as root, you’ll need to append –U username to all of your net ads commands – otherwise it’s going to try and authenticate root to the domain.
net ads info Display details on remote ADS server
net ads join Join the local machine to ADS realm
net ads testjoin Validate machine account
net ads leave Remove the local machine from ADS
net ads status Display machine account details
net ads user List/modify users
net ads group List/modify groups
net ads dns Issue dynamic DNS update
net ads password Change user passwords
net ads changetrustpw Change trust account password
net ads printer List/modify printer entries
net ads search Issue LDAP search using filter
net ads dn Issue LDAP search by DN
net ads sid Issue LDAP search by SID
net ads workgroup Display workgroup name
net ads lookup Perfom CLDAP query on DC
net ads keytab Manage local keytab file
net ads gpo Manage group policy objects
net ads kerberos Manage kerberos keytab
so, i can run net ads user –U smoir, enter my password and get a listing of the domains users! cool!
you could use "system-config-authentication" for a gui interface, but it's not going to give you all of the options and will write to the afore and after mentioned
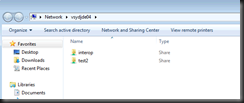
As you may have guessed, the final two stanza’s in smb.conf are the dirs that I’m sharing:
[test2]
path = /test
available = yes
browseable = yes
follow symlinks = yes
read only = no
public = yes
max connections = 0
[interop]
path = /u01/app/jdedwards/interop
available = yes
browseable = yes
follow symlinks = yes
read only = no
public = yes
max connections = 0
settings are pretty self explanatory, from windoze – I see
No comments:
Post a Comment